Webinar 9
Created: 1.3.2023, Last Edited: 14.3.2023
Our ninth webinar was in the typical jig-saw puzzle form. The goal of this webinar was to study legislation and demonstrate our competence regarding it. Unfortunately, I had to skip this webinar due to traveling to Rotterdam, however, I watched the recordings and participated in the activities afterwards by myself.
The webinar consisted of 4 distinct sessions: Confidentiality law, Principles of good administration, Ensuring a safe environment and Copyright and ownership. Not all recordings worked properly (for the entire duration), so I had to switch rooms when watching and will summarize presentations from 2 different rooms given by my colleagues who I will refer to as M, Y, Y&C and F.
M's session Confidentiality law
M's presentation was about confidentiality and the laws that relate to it. He began by introducing what personal data is: data that includes all information concerning an individual or his or her characteristics or living conditions if they can be identified as pertaining to the individual, his or her family or those living with him or her, such as name, personal identity code, contact details, information on studies, IP address, genetic information and marital status. [1]
M categorized the personal data into 3 groups: sensitive, general and details of criminal offences. Sensitive data includes details of racial or ethnic origin, political, religious or philosophical beliefs, health details, etc. General data includes the name, date of birth, address, area of work, CV, etc. They can be shared at a certain level with the permission of the person. The latter is information which can be used to deduce that a person has committed a criminal offence.
M then introduced a case study where a security breach in the matriculation examination board's online servers caused the personal information of nearly 8000 students to be leaked [2]. The leaked information included names, addresses, phone numbers, study information and social security numbers. With this case study in mind, M started a discussion and steered it in a way that it answered the following questions:
- How does a teacher consider the issue of privacy and data security in a teacher's work?
- What does "confidentiality" mean in practice?
- How long do you (or the school) must archive various documents?
- What can you reveal to your spouse/friends/co-worker/the student…?
Everybody agreed that it was indeed a serious incident and that the stolen information could be used with malicious intent (such as identity theft). The group also discussed about what data is sensitive and what not, like if the matriculation number leaks is not a big problem, compared to the social security number leaking instead. My colleagues also touched on Moodle and how the information there should be visible only to the teacher. Here I would like to add that in some cases the information could be shared forward to those who need to process it for various reasons (such as performing learning analytics). In this case, however, the data passed forward should be limited to the essential components: like if the goal is to assess a course, one can have access to the student feedback and the grades, but the individual student information is not necessary and should not be shared with the data processer. In practice, however, this may not be easily achievable, depending on the software involved, so students may be asked if their data can be used for facilitating learning. M also discussed that in some cases, very sensitive data should be stored within the institution's intranet instead of using cloud storage (like the Google Drive or Microsoft OneDrive).
M pointed out that any controller or processor must comply with all elements of Article 5 GDPR [3]. This includes lawfulness, fairness and transparency: any processing operation must be based on at least one of the six legal bases in article 6 of the GDPR [4]. The concept of fairness is quite vague in comparison and it depends on the institution. In either case, the data subject must be always aware of the processing that is going on (transparency). The data should only be used for the specific purpose (purpose limitation) and only the necessary information should be sent to the processer (data minimization). The data should also be kept up to date and stored as long as necessary, but as short as possible. M gave University of Turku as an example, where the teacher is obligated to reset their Moodle course (delete student information) after the theses have been evaluated, the course is concluded and after 6 months.
M also pointed out acts that function at the university level: VET (Chapter 11 – Processing and disclosing data) [5], UOAS (Section 21 - Administrative procedure and confidentiality) [6] and Data Protection Act (1050/2018)* [7]. According to these, all student personal information belongs to the student and therefore should be kept private. This includes assessment results, grades and demographic information. Individual privacy rights are recognized in the UN Declaration of Human Rights and in over 80 countries around the world. Teachers are responsible for holding student data in confidence and sharing it only with necessary parties. Confidentiality builds trust and is a big priority in educational settings. Teachers should establish clear security practices in their classrooms.
In the end there were nice discussions about practices at everyone's own institutions and changes that happened in time like grades becoming private in many countries, but it was not always the case. Something interesting that was mentioned is gossip, and that it's part of human nature, so, how problematic is discussing, for example, with your spouse about things that happen in the classroom. In general, the answer is no, things should be kept private, but if not revealing any personal information and simply describing some event at a general level should be acceptable. Work is a significant part of our lives and some information of what happens there should be shared with those near to us, I think. Sometimes, like in my case, we are both teachers, so discussing about some situation and figuring out how to act in different scenarios can be a benefit from work perspective as well.
I will share some personal experience with confidential data. It does not relate to a teaching environment per se, but the learnings could be useful nonetheless as they are general practices. When I was doing research, me and my team once worked together with SiunSote [8] and their database of sensitive health information from patients in Finland. We then had to sign a non-disclosure agreement (including us researchers and our students who may use the topic as a thesis of some sort). We had to be very careful who we share our findings with and one main problem was publishing results without revealing sensitive information. One way around this was to generate fake data that had similar properties as the original data. We demonstrated the applicability of proposed algorithms on it instead.
Y's session on Principles of good administration
Y's presentation was about good principles for administration. It started with an interactive session using jamboard, where each student wrote which principles they consider to be important. At the same time, students talked about why they consider those principles to be important.
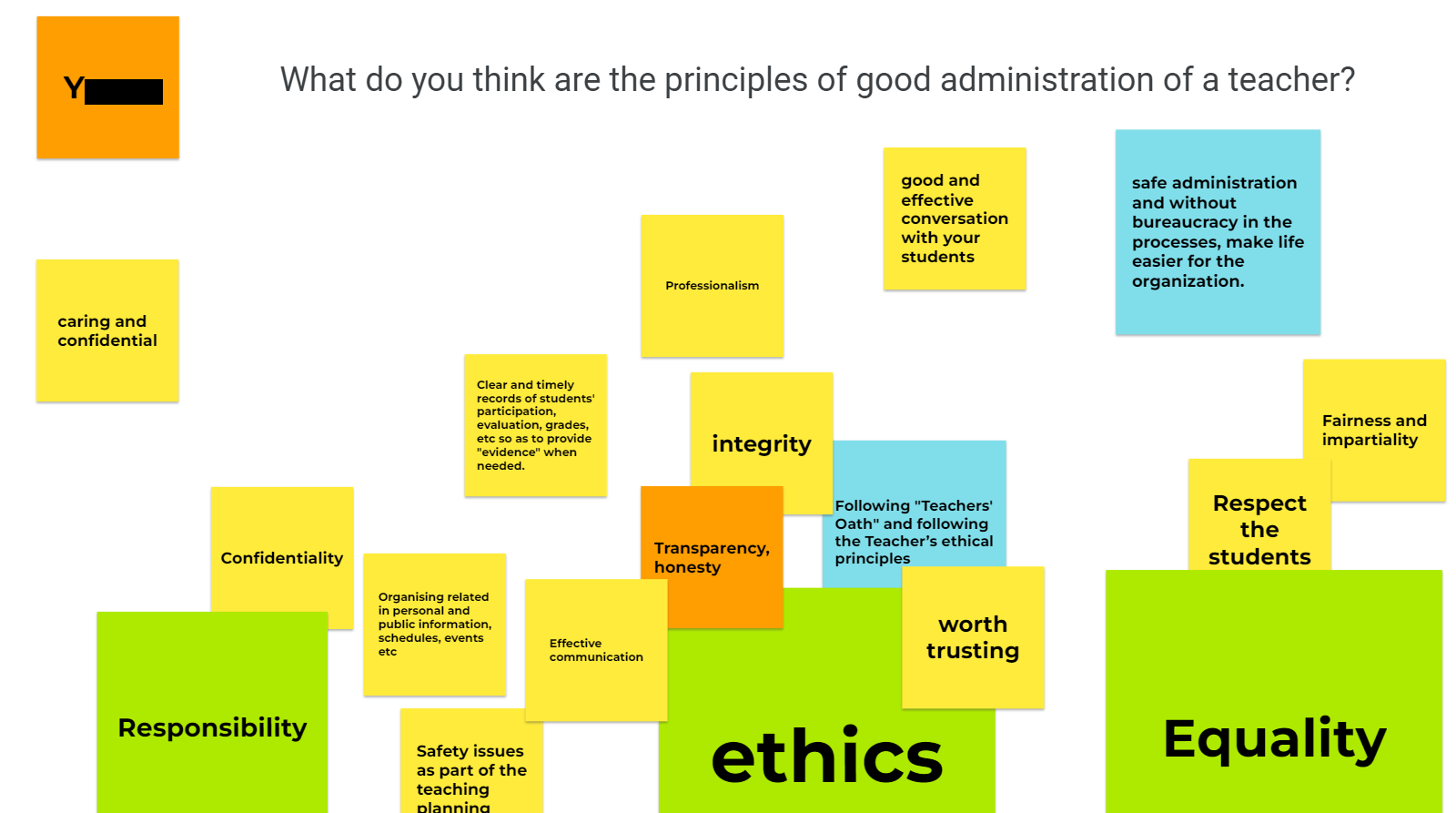
Figure 1: Jamboard created by the students
Meanwhile, Y gracefully performed a clustering of the submitted answers into 3 representative groups: Responsibility, Ethics (Integrity) and Equality (see Figure 1) and then proceeded to talk about laws related to the principles under consideration. These can be grouped into the 3 groups as follows:
-
Responsibility
-
Cooperation withworking life andbusinesses
- Section 4, Act on Vocational Education and Training [5]
- Section 6, Universities of Applied Sciences Act [6]
-
Student safety/ wellbeing
- Section 9, Administrative Procedure Act [9]
- Section 80, Act on Vocational Education and Training [5]
-
Special needs support
- Section 64, Act on Vocational Education and Training [5]
-
Cooperation withworking life andbusinesses
-
Ethics (Integrity)
-
Plagiarism
- Section 3, Constitution of Finland [10]
-
Feedback
- Section 51, Act on Vocational Education and Training [5]
-
Confidentiality
- Section 40, Constitution of Finland [10]
- Section 13, Administrative Procedure Act [9]
-
Plagiarism
-
Equality
-
Personal Development Plan
- Section 44, Act on Vocational Education and Training [5]
-
Use of proper and clear language
- Section 9, Administrative Procedure Act [9]
-
Accessible use of services
- Section 7, Administrative Procedure Act [9]
-
Personal Development Plan
One piece of reflection I can add here is that I am dissatisfied with tools we use to evaluate student assignments (Moodle). More precisely, I'm talking about the interface not being able to provide a view of the submissions that does not disclose the grades (see Figure 2). It is often the case that one student wants personalized feedback, or to showcase their submission during class. In that case I need to open Moodle and download the submission, however, doing so reveals the grades I give to students. I usually remember to switch off the projector during times like these, but it happens often and it's possible to forget that the projector is on during an active conversation that happens in class. The interface should have a way of concealing the information.
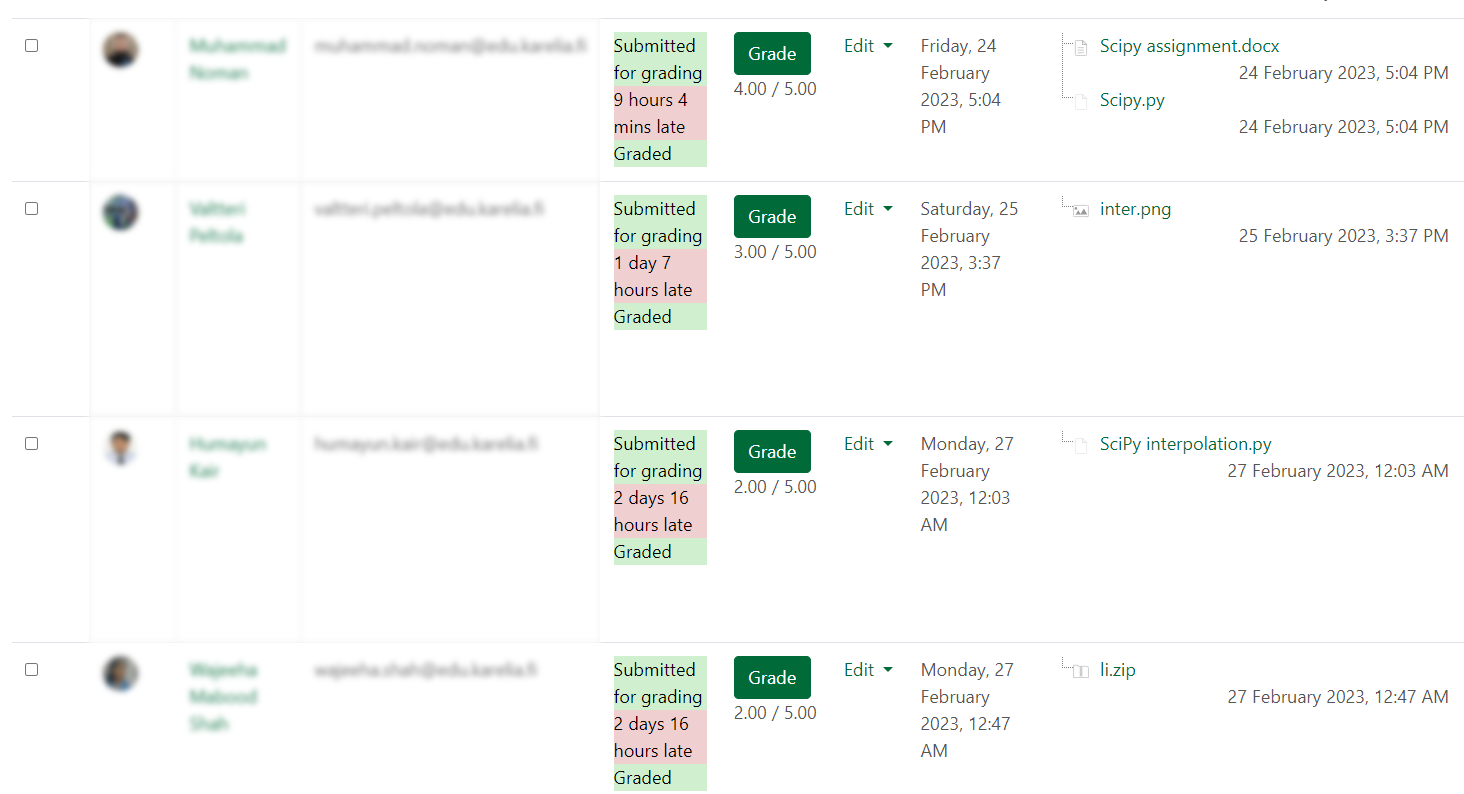
Figure 2: Moodle revealing grades when checking submissions
Y&C's session on Ensuring a safe environment
Y and C hosted sessions on how to ensure a safe environment and what things are regulated by the law. I feel that the content here was mostly repeating because the topic was addressed multiple times already (webinar 8 and learning days in oulu]. However, one thing I believe was interesting appeared during a discussion, when one student mentioned that there are many clear actions taking place to assure physical safety (inspecting fire extinguishers, assuring they are always in reach, etc) or legal safety (as discussed in the first section of this webinar) but the psychological safety is a topic that has less clear guidelines in practice. I liked learning what are the risks that individuals face when interacting with others. According to [11], these are:
- To be seen as ignorant when asking a question
- To be seen as incompetent
- To be catalogued as negative when criticizing events
- To be seen as instructive when asking for feedback
F's session on Copyright and ownership
F began her session on copyright and ownership by explaining what a teacher needs to know about copyright law. She explained how the copyright is a protection of creative work and it gives the author the right to govern his or her work. The copyright protects the appearance and expression of the work, but it does not protect the information, idea, subject, plot or structure contained in the work. Copyright starts when the work is finished, and is valid for the lifetime of the author and an additional 50-70 years depending on the specific case. The author may pass on some of his or her rights to someone else.
F then explained how a teacher should act to respect copyright laws; if a teacher wants to use copyright-protected materials he or she needs to get the consent from the author in advance. Otherwise, using open-access materials is always an option and you can find material like that by selecting the correct options in search engines, but the teacher needs to always properly cite where the material was taken from. Teachers own the right to the learning materials they produced and copyright-protected materials can be used for educational purposes in accordance with the copyright act [12] and an agreement between Kopiosto [13] and Finnish institutions of higher education. Kopiosto is an organization that offers an easy and responsible way to use copyrighted publications and audiovisual works. They also ensure that professionals in the creative industry receive fair remuneration for the use of their works.
F also talked about copying material in higher educational institutions and that there are limits to photocopying, scanning and printing. These upper limits are usually 20 pages per publication or a maximum of 50% of the publication for printing and 20% for scanning. F then hosted an interactive session on Socrative.com where she assessed our understanding of copyrights with 10 questions related to 10 different scenarios. They were quite tricky but quite informative, especially when making a mistake because we got to see the explanation for the correct answer.
The discussion at the end was interesting, especially when one of the students brought up the topic of memes and if they violate copyright. I think they are an example of 'things spiraling out of control' because we do not have technology in place to detect and ban their use. I can personally relate to this and copyright in general and know how it changed over the years and how websites evolved alongside the laws. For example, in the early days of YouTube, many people (including myself) were posting self-made anime music videos or music videos with cutscenes from various movies. In the beginning, people could upload this content without consequences (it was seen as transformative work). In time, however YouTube had to abide by the law and developed ways of handling these situations. First it started by detecting that the material already exists somewhere and flagged the video. After 3 such incidents, the channel was deleted automatically. This was a harsh way of handling it, however YouTube did what it could at that time to avoid legal consequences. Nowadays, the solution is more sophisticated: the algorithm recognizes that the content belongs to someone else (the singer, or an entertainment business) and any monetization gained from the individual using the copyrighted content will be redirected to the rightful owners of the content instead. There is a fair-use limit of 10 seconds (if you use content that is less than that threshold, it should be OK), but the laws are changing all the time and avoiding content like this entirely is the safest approach, in my opinion. Here is an example video I made that includes 2 musical pieces from others (Darude and The Weeknd). I can not monetize this video because the segments are just a little bit over 10 seconds long. YouTube does offer the possibility of replacing those audio segments with something else, so monetization would be enabled, but I made this video in part to test these verification algorithms and am not interested in monetization so I keep it as such (see the video below, artist information can be seen in the video description).
Another experience I have with copyright relates to research and collecting data off the internet to create datasets. Once we collected a dataset of service providers in Finland like restaurants, bars, etc. We intended this dataset to be used for research in natural language processing and made it publicly available for other researchers as well [14]. These websites were publicly available and we thought that collecting this information was not a problem. The way we were storing it on the university server, however, was problematic, allowing search engines (like Google) to find and index our local copy and sometimes it would appear on search ahead of the original address of the service. This resulted in few direct complaints which forced us to store the data a different way and fix the problem.
F also pointed out to the useful Finlex Data Bank [15] which is a trusted source with information about copyright laws in Finland with a focus on teaching. Another way to understand copyrights is to participate to events organized by educational institutions like the one organized by Oulu university (we have similar ones going on at Karelia as well), but what was new to me was Kopiraittila: a game that teaches copyright law [16].
REFERENCES
- https://teaching.helsinki.fi/instructions/article/data-protection-teachers
- https://yle.fi/a/3-10066101
- https://gdpr-info.eu/art-5-gdpr
- https://gdpr-info.eu/art-6-gdpr
- https://www.finlex.fi/en/laki/kaannokset/2017/en20170531.pdf
- https://www.finlex.fi/fi/laki/kaannokset/2014/en20140932_20200000.pdf
-
https://www.finlex.fi/en/laki/kaannokset/2018/en20181050.pdf
* Note, I'm citing here instead of the original, because:
“The Personal Data Act 523/1999 has been repealed by the Data Protection Act 1050/2018.” - https://www.siunsote.fi/en/web/english
- https://www.finlex.fi/en/laki/kaannokset/2003/en20030434.pdf
- https://oikeusministerio.fi/en/constitution-of-finland
- Edmondson, Amy C., Roderick M. Kramer, and Karen S. Cook. "Psychological safety, trust, and learning in organizations: A group-level lens." Trust and distrust in organizations: Dilemmas and approaches 12, no. 2004 (2004): 239-272
- https://www.finlex.fi/en/laki/kaannokset/1961/en19610404.pdf
- https://www.kopiosto.fi
- https://cs.uef.fi/mopsi/titler
- https://www.finlex.fi/en/
- https://kopiraittila.fi/